Protection for how you work
Data is a valuable resource in today's environment. It drives our digital economy and powers our
productivity, but it can also have a negative impact on us.
You cannot protect everything from everyone.
Therefore, you must implement a risk-based approach to data protection and security.
That way, we can not only optimize our use of data to generate revenue, but also prevent harm or
disasters.
Data breaches continue with regularity and compliance mandates get more stringent, organizations
need to protect their sensitive data in both local and cloud environments.
Not just because you’ve lost a valuable asset, but your reputation, and market cap could be at
stake.
Utimaco helps organizations move past silos of encryption and crypto-management solutions to attain
central and uniform deployments of data protection solutions and prepare your organization for the
next security challenge and new
compliance requirements at the lowest total cost of ownership(TCO).
Our advanced data discovery, data encryption, key management, network encryption, hardware security
module and data protection on demand solutions enable customers to protect and remain in control of
their data wherever it resides –
across cloud, on-premises and hybrid IT environments.

Data privacy
Protect sensitive information. Personally identifiable information ("PII") is regulated and must be kept confidential, otherwise there may be a risk of loss of trust, regulatory actions, brand integrity or competitive advantage.
Data security
Strong security controls, continuous activity monitoring, and automatic protection measures should be used to prevent going astray and minimize risks.
Information integrity
Whether you’ve got an inadvertent user virus, or malicious malware attack—you need access to data when you need it. Failure may result in fines or wasted time due to re-work.
Your data, where it should be
-
Utimaco solutions offer you peace of mind knowing you'll access critcal data whenever it is required, and the protecting controls will be available to reduce risks from human error, attack, or disaster.
-
Enable digital transformation
Understand your data and how it flows and the associated risk level. Classify data to inform cloud migration and investment opportunities
-
Protect your brand
Automate corrective actions to protect data, or revert out-of-policy changes.
-
Confidential & available
Ensure data is easily recoverable in the event of disaster or malware attack.
-
Risk management
Perfect security’s a myth. Prioritize what you’re protecting to ensure users follow rules to mitigate risk and harm.
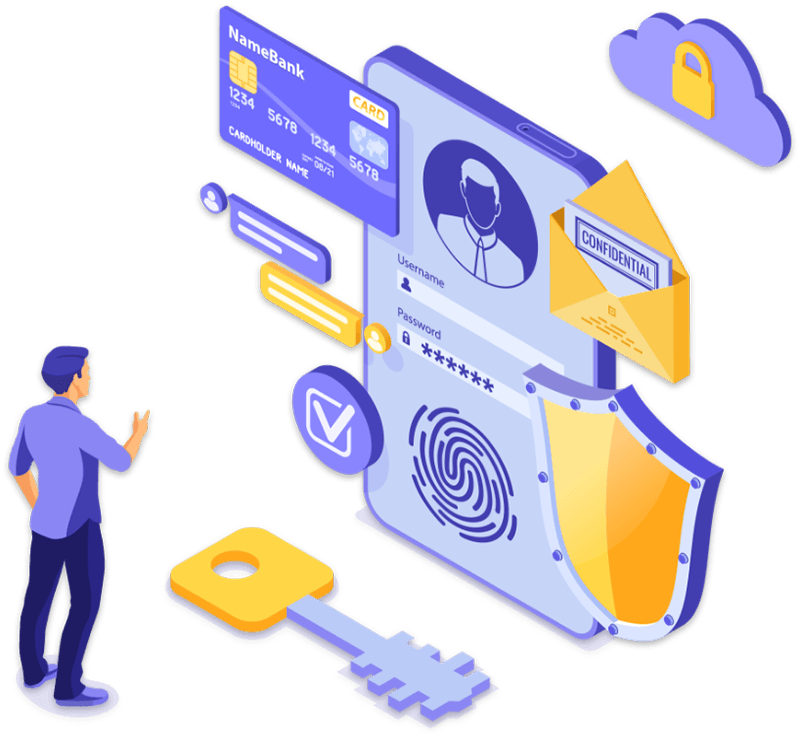

Authentication
Authentication is a process that verifies the identity of a user or device.
It can be part of a broader identity and access management process that continuously
authenticates subjects in a system.
Is a subject really what it claims to be?
This is what the authentication process confirms by means of various authentication
mechanisms
Block-safe
Utimaco Block-safe secures sensitive identity, keys and data used in blockchain-based distributed computing platforms. The FIPS 140-2 L3 compliant HSM provides unrivaled key generation and protection for Blockchain specific elliptic curves. It protects and manages encryption keys needed for key derivation within the tamper-resistant hardware device.

Key Management
Offered in both on-premise hardware and virtually,
Utimaco Enterprise Secure Key Manager (ESKM) & Virtual Enterprise Secure Key Manager (vESKM)
provide centralized key management, securing encryption keys with consistent policy controls
for data at rest.
Data Rentention Suite
Data Retention Suite(DRS) has been designed as a carrier-grade system to enable fast
and secure access to retained data by authorized agencies.
DRS enables network operators and Internet service providers to easily comply with recent
telecom regulations for data retention.

KeyBRIDGE
The KeyBRIDGE platform extends a simple, intuitive interface for managing and distributing cryptographic keying materials across a broad spectrum of use cases. Organizations can securely store, distribute and access sensitive keying material and secret data within a single, centralized location.

Privacy Shield
The transatlantic data transfer is not yet secure: ongoing discussions and criticism from within the EU, the U.S. “America first” initiative, review of proficiency and potential shortcomings as well as GDPR. Companies are, on the one hand, advised to stay up-to-date and on the other hand, turn towards encryption & HSMs as the solution to comply with privacy and data protection requirements.

PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) defines a set of security standards. With these companies that accept, process, store or transmit credit/debit card information can maintain a secure environment and protect cardholders against misuse of their personal information. One of the most efficient ways of complying with PCI DSS is to use HSMs.

eIDAS
On July 1st 2016, the electronic identification and trust services regulation,
more commonly known as eIDAS, replaced the 17-year old eSignature Directive 1999/93/EC
and became directly applicable in 28 EU member states.
As an HSM manufacturer,
Utimaco is at the forefront of defining related technical requirements and achieves
conformity with eIDAS requirements.

GDPR
The new EU data protection framework,
also referred to as the General Data Protection Regulation (GDPR) has been in place since
25th May 2018.
It came with potential heavy fines and applied to every company operating in Europe.
Encryption is mentioned as the only technology recommended to achieve compliance.
Want your data more secure and protected?
Get in touch with us at info@utimaco.com to discuss how we may help you achieve that. Together we will find a solution that caters to your needs.